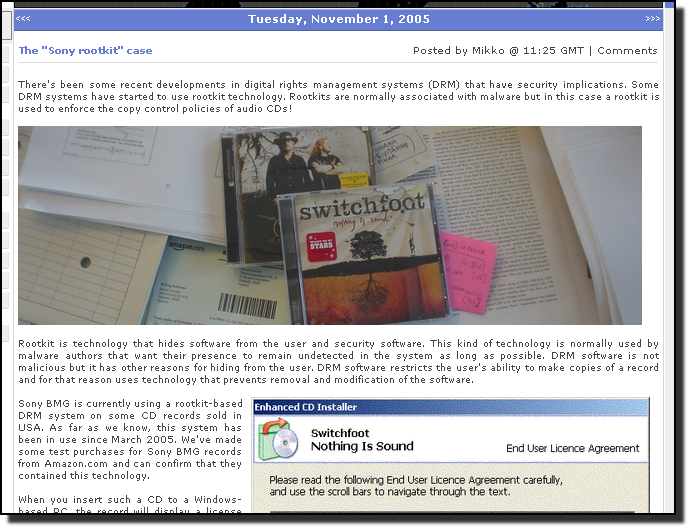
When such audio CDs were played on a Windows computer, a Digital Restrictions Management component was installed and hidden by a tailor-made rootkit. The rootkit would not just hide Sony BMG's own software, but any program that would contain the characters $sys$ in its file name. The rootkit was so effective that at the time, most antivirus programs were not be able to scan the hidden files. As an end result, virus writers started releasing their malware with filenames that would cause the Sony rootkit to hide them automatically, if it was installed.
This was a huge deal, and Sony's reaction was a good example of how not to handle a PR crisis.

We originally found the rootkit in September 2005, but the news broke five years ago, on the first of November 2005, when Mark Russinovich went public with the case.
 By far the best write-up on the whole incident was published in an article by MIT Technology Review, complete with comments from Mika Ståhlberg and Santeri Kangas from our labs.
By far the best write-up on the whole incident was published in an article by MIT Technology Review, complete with comments from Mika Ståhlberg and Santeri Kangas from our labs.Not all security vendors agreed immediately that Sony was wrong. Our two favorite quotes regarding the whole incident are here:
From The Inquirer:
If you want to find a trustworthy security vendor, I would recommend looking for ones that stood up on the Sony malware DRM infection issue and said 'this is bad' early and loudly. F-Secure comes to mind, but there are others. The ones that said 'grumble, mumble, maybe, sorta' a week later are not what you want to have protecting your machines.
From Bruce Schneier:
Perhaps the only security company that deserves praise is F-Secure, the first and the loudest critic of Sony's actions.
Then again, some people say that if you listen to Celine Dion, you deserve to get infected…










 Microsoft has released a very large set of updates to Windows, IE, Office. the .NET Framework and Microsoft server software.
Microsoft has released a very large set of updates to Windows, IE, Office. the .NET Framework and Microsoft server software.